You are here
System Activity
The System Activity monitor keeps track of various system processes such as upgrades, and more importantly the IP address from where the upgrade was run. This helps your organization fulfill the PCI DSS Cross Reference/Index Requirement 10: Track and monitor all access to network, where you are required to track and monitor all access to network resources and cardholder data. Logging mechanisms and the ability to track user activities are critical for effective forensics and vulnerability management. The presence of logs in all environments allows thorough tracking and analysis if something goes wrong. Determining the cause of a compromise is very difficult without system activity logs.
For more on the PCI DSS Cross Reference/Index, click here.
For more on Requirement 10 of PCI Compliance, click here.
The System Activity Monitor is accessed under the Setup>>System Activity menu.
The System Activity window will open.
Enter the date range for which you wish to examine the logs.
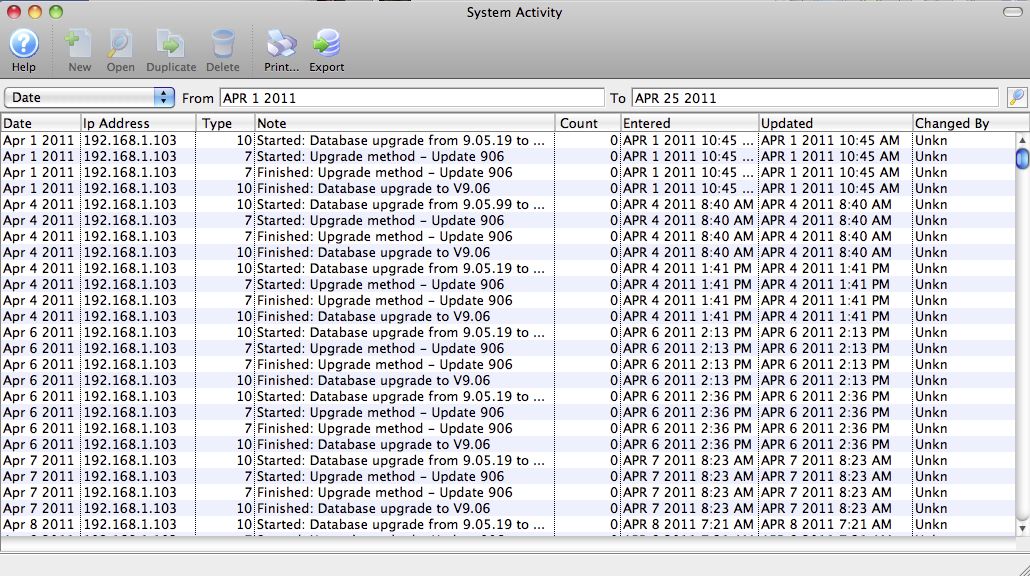
Parts of the System Activity Window
Prints a report of the log file. |
|
Exports the logfile to either a text file or Excel. |
|
Date |
Date the particular activity took place. |
IP Address |
The IP address from where the activity was requested. |
Type |
The System Activity Record Type |
Note |
Description of the activity. |
Count |
Is a generic/multi-purpose field: |
Entered |
Date and Time the activity was initiated. |
Updated |
Date and Time the activity was completed. |
Changed By |
Log on name of the employee (if known) initiating the activity. |