You are here
Diffie Hellman Parameter File
What is Diffie-Helman?
Credit: Stack ExchangeDiffie-Helman is a way of generating a shared secret between two people in such a way that the secret can't be seen by observing the communication. That's an important distinction: You're not sharing information during the key exchange, you're creating a key together.
This is particularly useful because you can use this technique to create an encryption key with someone, and then start encrypting your traffic with that key. And even if the traffic is recorded and later analyzed, there's absolutely no way to figure out what the key was, even though the exchanges that created it may have been visible. This is where perfect forward secrecy comes from. Nobody analyzing the traffic at a later date can break in because the key was never saved, never transmitted, and never made visible anywhere.
The way it works is reasonably simple. A lot of the math is the same as you see in public key crypto in that a trapdoor function is used. And while the discrete logarithm problem is traditionally used (the xy mod p business), the general process can be modified to use elliptic curve cryptography as well.
But even though it uses the same underlying principles as public key cryptography, this is not asymmetric cryptography because nothing is ever encrypted or decrypted du ring the exchange. It is, however, an essential building-block, and was in fact the base upon which asymmetric crypto was later built.
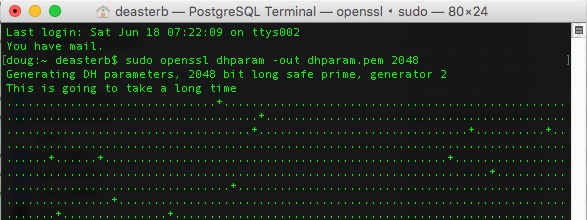
How to create your Diffie Helman parameter file
Since the Diffie-Helman parameter file is a way of creating a shared secret at the start of the cryptographic process, you can change it as often as you want, completely independently of the TLS certificate. It is quite easy to do so.
| Macintosh |
This needs to be done using Terminal:
|
| Windows | Please ask Arts Management support to make one for you or find a Macintosh. |