Main Firewall
We only recommend a router/firewall that has the ability to isolate the apache computer (i.e. designate an ip address for the DMZ).
 |
Your firewall need to restrict connections between untrusted networks and any system components in the card holder environment PCI requirement 1.2.
|
|
When you need to set up firewalls on computers, the built in firewall on windows is very flexible. On macOS, do not manage the built in firewall via System Preferences on servers - instead, consider using a tool like Murus Firewall to unlock the power of the macOS PF Firewall. |
Firewall/Router Rules
 |
This diagram identifies which traffic is required for Theatre Manager to work in the card holder environment per PCI requirement 1.2.1
Any traffic not required should be denied - and the router should be set to 'deny all' unless explicit permission is given. |
|
All traffic is TLS 1.2 or better, including to and from:
|
In the example below, we'll refer to IP addresses
- in the office VLAN as 192.168.1.x
- in VLAN2 (containing wireless devices and/or machines not subject to PCI) as 192.168.2.x
- and use 192.168.1.10 as the inside address of the DMZ where the Web Server resides, protected on both sides by firewall rules. The outside IP address (internet) also authenticated and verified using an TLS Certificate.
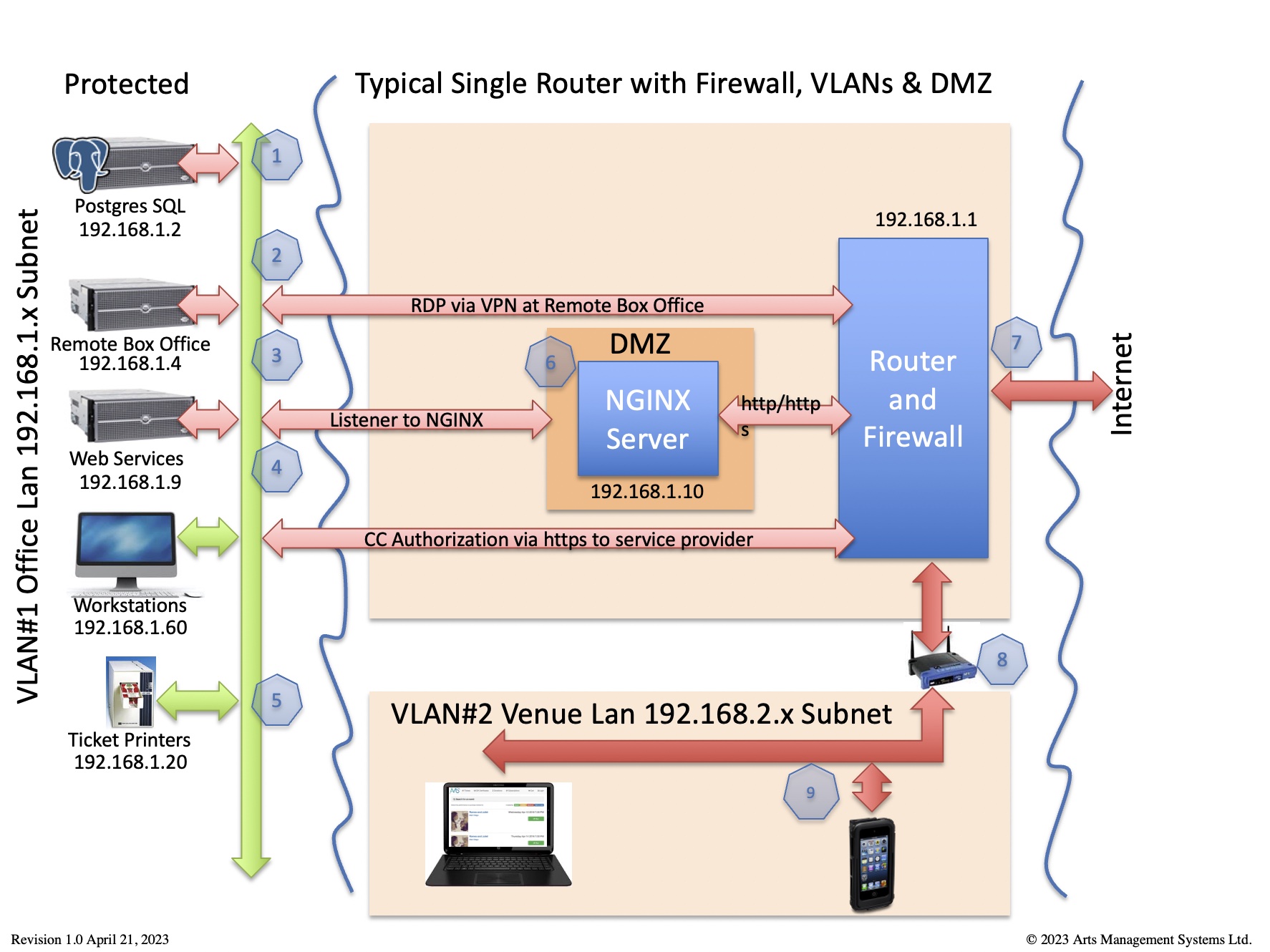
|
|
If you prefer to view the firewall rules from the perspective of specific ports, please refer to ports used by Theatre Manager
| Item | Machine and Purpose | Subject to PCI | Virus S/W | Inbound Port Rules | Outbound Port Rules |
| 1 | PostgreSQL server
database |
depends | no* |
|
|
| 2 | Remote Box Office via VPN (or terminal server) |
yes | yes* |
|
|
| 3 | Web Services (TM Listener) | yes | no* |
|
|
| 4 | Box Office Workstations | yes | yes* |
|
|
| 5 | Ticket Printer | no | n/a |
|
|
| 6 | Web Server (NGINX) | yes | yes* |
|
|
| 7 | Outside of Firewall | no | n/a |
|
|
| 8 | Internal Wireless Router | no | n/a |
|
|
| 9 | Venue Lan
computers not handling credit cards |
no | yes |
|
|
| 10 | wireless ticket scanners | no | n/a |
|
Ports used by Theatre Manager
- ports 80 & 443 externally for web sales.
- Outgoing port 443 for credit card authorizations
- port 37 for a time server
- port 53 for MX record lookup via a DNS server
If you prefer to view the firewall rules from the perspective of specific machines, please refer to ports used by each machine
| Port | Meaning | Use | Security Note | ||
| 25 (or 465 or 587) | SMTP | Outgoing | TM Server uses this for email for web sales, eblasts and meeting scheduling. note: Workstations do not send emails and do not require access to SMTP server.
Alternate SMTP ports can be used as TM supports (startTLS and other security) You may wish to place a small SMTP server (like Exchange) within your network so that TM talks to it and allow it to relay to the internet. This also controls outgoing access. |
||
| 37 | NTP Time Server | Outgoing | OSX and Windows machines use this to syncronize clocks. All machines should be able to synchronize with an NTP server so that transactions and audit logs are accurately recorded when the happen per PCI 10.4 compliance | ||
| 53 | DNS and MX lookup. | Outgoing | This is used to verify email and web domains during the data entry process to improve data quality | ||
| 80 | HTTP | Incoming and Outgoing | Incoming is only required to the Web server.
Outgoing for workstations to communicate to:
|
||
| 443 | HTTPS | Incoming and Outgoing | Incoming is required for web sales.
Outgoing is required for TM Server and TM Workstations for
|
||
| 110 (or 993) | POP3 | Outgoing | Facility Management module only: TM has a scheduling function that lets users set up calendar event and send the invitations to users, patrons and volunteers.
The port is used by TM workstation and Server, and only email with valid outlook or iCal attachements are read. All others are discarded. No user checks this email address. Theatre Manager supports alternate POP3 ports if you prefer. |
||
| 5000 | Web Services | Internal | The Web Server load balancer communicates to Theatre Manager Web Services on port 5000 | ||
| 8111 | Web Template Server | Internal | This internal port on the web server is a Virtual host used by web services to obtain the custom web page templates from the htdocs folder for merging. It is also used by workstations to obtain web page templates used to send double out-in confirmations as per CASL (Canada's Anti Spam Law). | ||
| 8201 | Cache Server | Internal | This internal port is used for caching data shared between web service processes. | ||
| 5432 | Postgres | Internal | This is the standard port for the Postgres database server and is only used within the LAN. Postgres's pg_hba.conf configuration file specifies the IP address ranges (or specfic IP's) that can communicate with the database server. If a machine is not permitted to talk, postgres will does not respond.
Traffic from workstations to Postgres is via TLS 1.2 |
||
| 10001 | Ticket Printer | Internal | Workstations send a string of characters to print a ticket. The printer responds with status requests as need be.
No outside machine needs access to a ticket printer. |
||
| xxxx | Terminal Server & Remote Access | Incoming | A secure connection from the remote box office to the firewall is recommended for security purposes. RDC and Terminal Services establish secure connections. VPN is additional security. |
PostgreSQL Server
Only this port needs to be open on this server. All other inbound ports can be closed in the operating system. The port can be changed by editing the Postgresql.conf file, or during the install.
Misc Recommendations
- File and email services for the network must be placed on a separate machine from the database server.
- Turn off windows auto updater. Instead, perform regular maintenance at a time of your choosing (every second Monday for example, more often if the news reports critical viruses) to download and install updates. For 24/7 web sales service, it is important that the Postgresql server run constantly and only be updated at a time of your choosing.
- On OSX, turn off Software Update and run regular maintenance every second week, similar to Windows Environment. There is far less risk on unix based systems for virus attack vectors.
 |
Deploy anti-virus software on all systems commonly affected by malicious software, particularly personal computers and file servers. PCI requirement 5.1 |
|
Since postgres is implemented on a stand alone machine (per PCI requirement 2.2.1), we recommend that you DO NOT install virus software on the PostgreSQL Server. If you must, then do it under very controlled circumstances.. Never allow the virus scanner to scan the actual postgres database directories for traffic because virus scanners severely affect performance when many files are changed rapidly (as in a stand alone database server). If you absolutely must scan all files, scan the database folder at very off peak hours. |
TM Listener - Web Services
In all cases, you specify the ports to talk to listeners within the TM Director interface.
Simple Setup for Load Balancing
In the simple setup situation, you just need to open port 5000 to each TM listener. When any message is received by the second gen listener externally on port 5000, it load balances internally on ports local to the machine (5001-5010, 5111, 5201-5210).
Each second generation listener machine needs to be able to talk to the designated TM Web Listener machine to retrieve web pages.
Custom Setup for Load Balancing
In the custom setup, the web processes can listen on
- Second Generation Listener:
- port 5000 (like the simple setup for load balancing) -or-
- ports 5001-500x where you specify the load balancing on the TM Web server for high performance throughput -or-
 |
Deploy anti-virus software on all systems commonly affected by malicious software, particularly personal computers and servers PCI requirement 5.1
You can install anti virus software on the TM Server - but may need to exclude the TheatreManagerServer program directory and all traffic to port 5432 on the postgres server. Since the web services run as a service, there is limited need to log into the machine. It should not be used for any other purpose and listens only to the API's from the TM server, so you may only need periodic file scanning at night if you do not join a domain and/or limit people who can access it. |
