Firewall/Router Rules
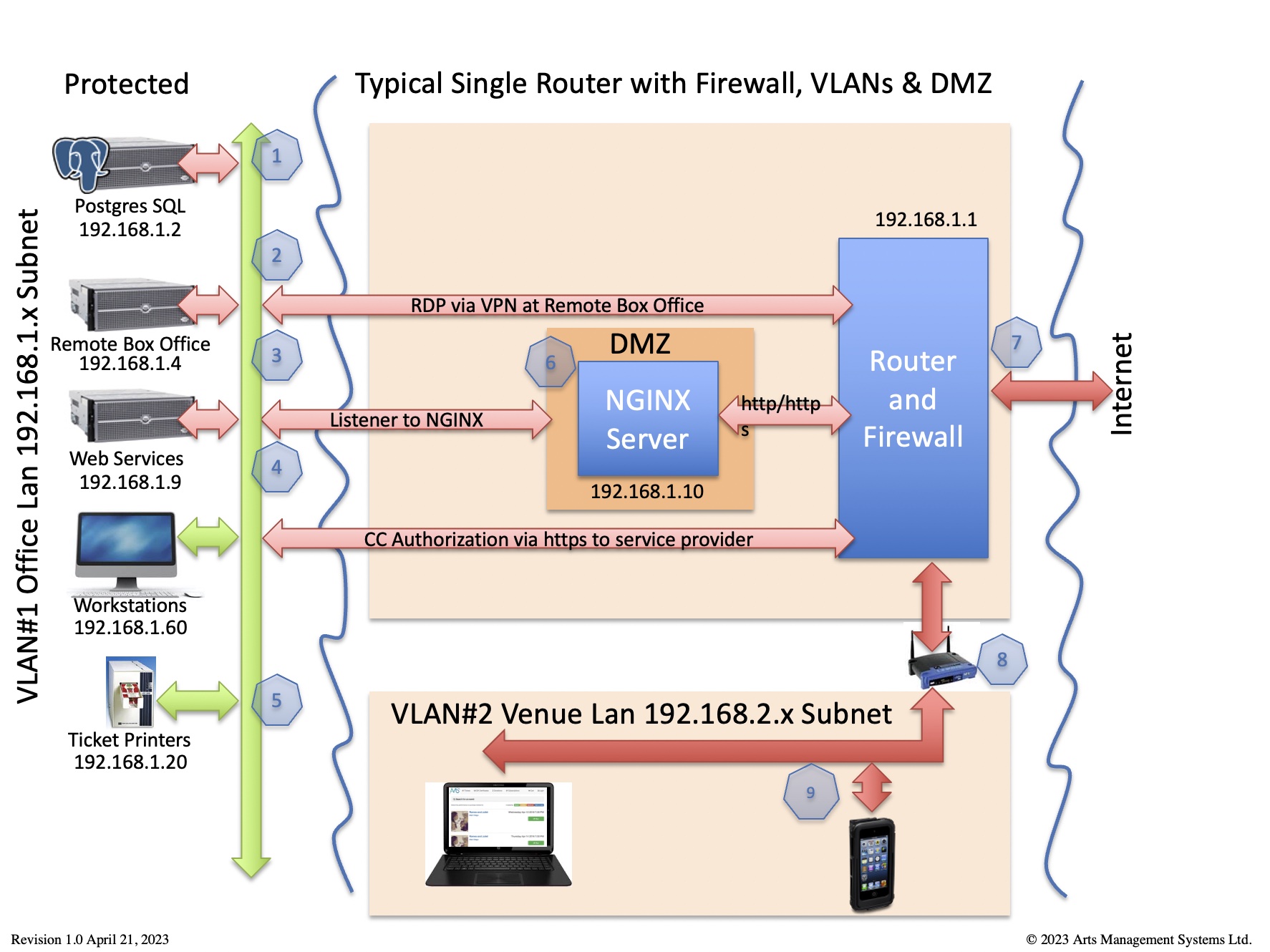
The main router/firewall is protection from the outside world. If the router has DMZ capability, please set up the DMZ IP address to have the same subnet range as the office LAN. This will make it easier to scale up web listeners that talk to the Web Server.
 |
This diagram identifies which traffic is required for Theatre Manager to work in the card holder environment per PCI requirement 1.2.1
Any traffic not required should be denied - and the router should be set to 'deny all' unless explicit permission is given. |
|
All traffic is TLS 1.2 or better, including to and from:
|
In the example below, we'll refer to IP addresses
- in the office VLAN as 192.168.1.x
- in VLAN2 (containing wireless devices and/or machines not subject to PCI) as 192.168.2.x
- and use 192.168.1.10 as the inside address of the DMZ where the Web Server resides, protected on both sides by firewall rules. The outside IP address (internet) also authenticated and verified using an TLS Certificate.
|
|
If you prefer to view the firewall rules from the perspective of specific ports, please refer to ports used by Theatre Manager
| Item | Machine and Purpose | Subject to PCI | Virus S/W | Inbound Port Rules | Outbound Port Rules |
| 1 | PostgreSQL server
database |
depends | no* |
|
|
| 2 | Remote Box Office via VPN (or terminal server) |
yes | yes* |
|
|
| 3 | Web Services (TM Listener) | yes | no* |
|
|
| 4 | Box Office Workstations | yes | yes* |
|
|
| 5 | Ticket Printer | no | n/a |
|
|
| 6 | Web Server (NGINX) | yes | yes* |
|
|
| 7 | Outside of Firewall | no | n/a |
|
|
| 8 | Internal Wireless Router | no | n/a |
|
|
| 9 | Venue Lan
computers not handling credit cards |
no | yes |
|
|
| 10 | wireless ticket scanners | no | n/a |
|
