Troubleshooting web sites
Browser unable to access web site or security issues
ALWAYS Test the TLS certificate
To Do This:
- Go to the web site ssllabs.com/ssltest and run a test of the ticketing URL to see what is reported. Enter the URL and make sure keep the results private by not showing them on the boards.
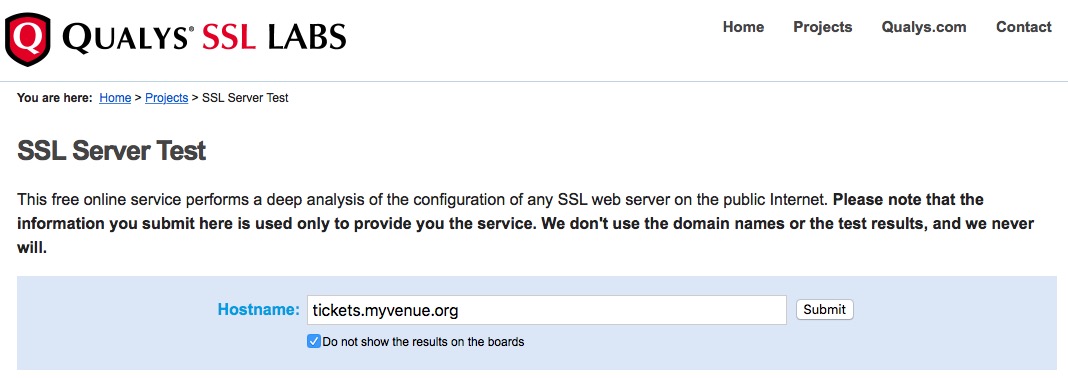
- Review the results as below. At this time, make sure that:
- the site gets at least an 'A' score
- there are no unexplainable comments
- only TLS 1.2 and later is supported with SHA 256
- and that the users browser is in the list of acceptable/current browsers. Anything older, will not connect
Review the results of the TLS Certificate Test
The ENTIRE document tells us something about what browsers the web site will support and how they will support those browsers. The key parts are described as follows.
Overall Score
The overall Score is near the top and may have a message or two. This looks like the image below.
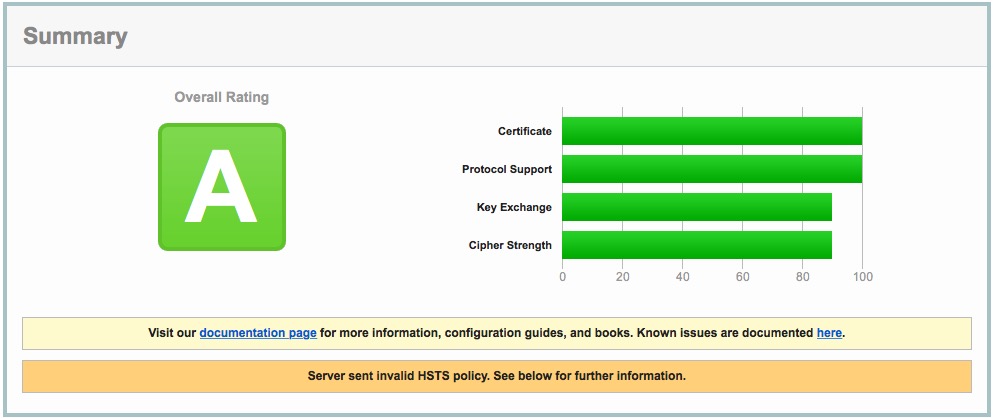
Configuration Protocols
Review the protocols supported. This will change from time to time and only get stronger. As of Sept 2016, the PCI council and the browser makers (Google, Safari, Firefox, etc) are all pushing TLS. The minimum current safe browsing standards are TLS 1.1 or TLS 1.2. Anything lower means your web site is vulnerable to some web attack. TM Server is designed to only allow TLS 1.2 at this time - because of PCI.
Please ensure that only TLS 1.2 is enabled.
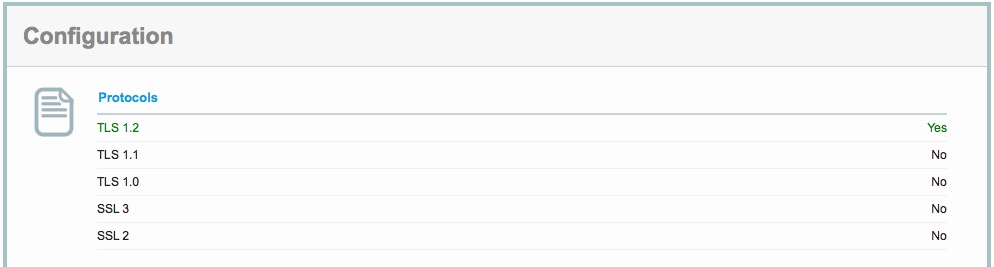
Review the browsers supported
A little further down the report is a complete list of many different browsers. The list includes many older ones and all the current versions and tells you:
- Which browsers cannot connect. eg IE 6, 7, 8, 10 & Safari on OSX 10.8.x and earlier cannot use the web site - simply because the browsers do not support the minimum secure protocol as recommended by PCI.
- For those browsers that connect, it tells you with protocol and (TLS 1.2) and level of encryption (RSA 2048/SHA 256) with ECDHE (Elliptic Curve Diffie-Hellman Exchange) protocol for negotiating the key exchange between the web site and browser (very secure).
Microsoft IE 11 unable to access Web Site
 |
In general, IE 11 cannot distinguish the various security methods automatically like other browsers and need to be told to ignore SSL 2.0: |
- Microsoft indicates this is an issue if both SSL 2.0 and TLS 1.2 are enabled as security options in IE 11
- The solution, they say, is to disable SSL 2.0 (which is normally disabled by default and is no longer supported by any commerce web site
If your customers ask, this may be their problem.
Patrons can't use an email address

Why can't a patron use an email address?
If a person cannot create an account with a specific email address within Theatre Manager web sales, it is for one of 3 reasons:
- The email address is already in the system for one patron and the only course of action is to request a forgotten password
- The email address is in the system but attached two TWO OR MORE patrons in different households. TM allows sharing of an email within a household, but not across households. So, TM denys use of that email address until the box office sorts out who really owns it using the find duplicate email address function. It could be that people need merged from two separate data imports, or one person should not have it.
- we cannot find the domain name or there is no MailBox (MX) server for the email address. Perhaps they've specified something like ImBad@rotten.org - which really doesn't exist, so we can't create it.
 |
Unless you have changed messages in tmError.txt to the contrary, use the above checklist to check email address rejection.
The forgot my password web page shows this generic message. |
Why can't the messages be more specific?
Can Theatre Manager actually distinguish amongst the types of errors above? yes it can - there are actually separate error messages in the tmError.txt for all these situations. However, they just happen to say the same thing 'Email address can't be used'
Why is that? The PCI council (Visa and Mastercard) make all the rules as to what kinds of applications are compliant. Theatre Manager is audited and approved by the PCI council to make sure we follow the rules of safe storage of their credit card data and safe online web sales following their prescribed audit cycles.
One of the rules concerns privacy. A web site should NOT give back any information about accounts and login credentials. The thinking is that if there is an easy way for a bad buy to find out which email addresses are in a system, they are half way there to logging in. Thats because people tend to use the same id's and passwords at many sites. So, if they've cracked another site, then its easier to infiltrate venues that give out this kind of knowledge.